SecuLetter was in Riyadh, Saudi Arabia LEAP 2024 with our partner SLNEE IT! SecuLetter and SLNEE worked for not only exhibition, but also for our new Secure Cloud Email Platform, 'DEOM + SLE'. Feel free to contact us if you want more information on our new service.

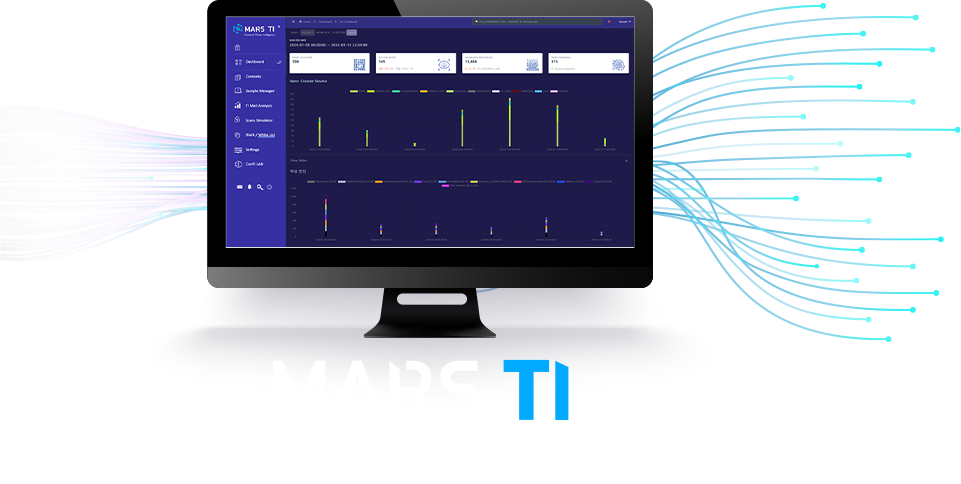
The Best Detection Rate in Industry Accurate diagnosis rate and reduce false positives and negatives. KISA certified for industry-leading malware detection rates