Digital Content is ESSENTIAL
in Business Communication
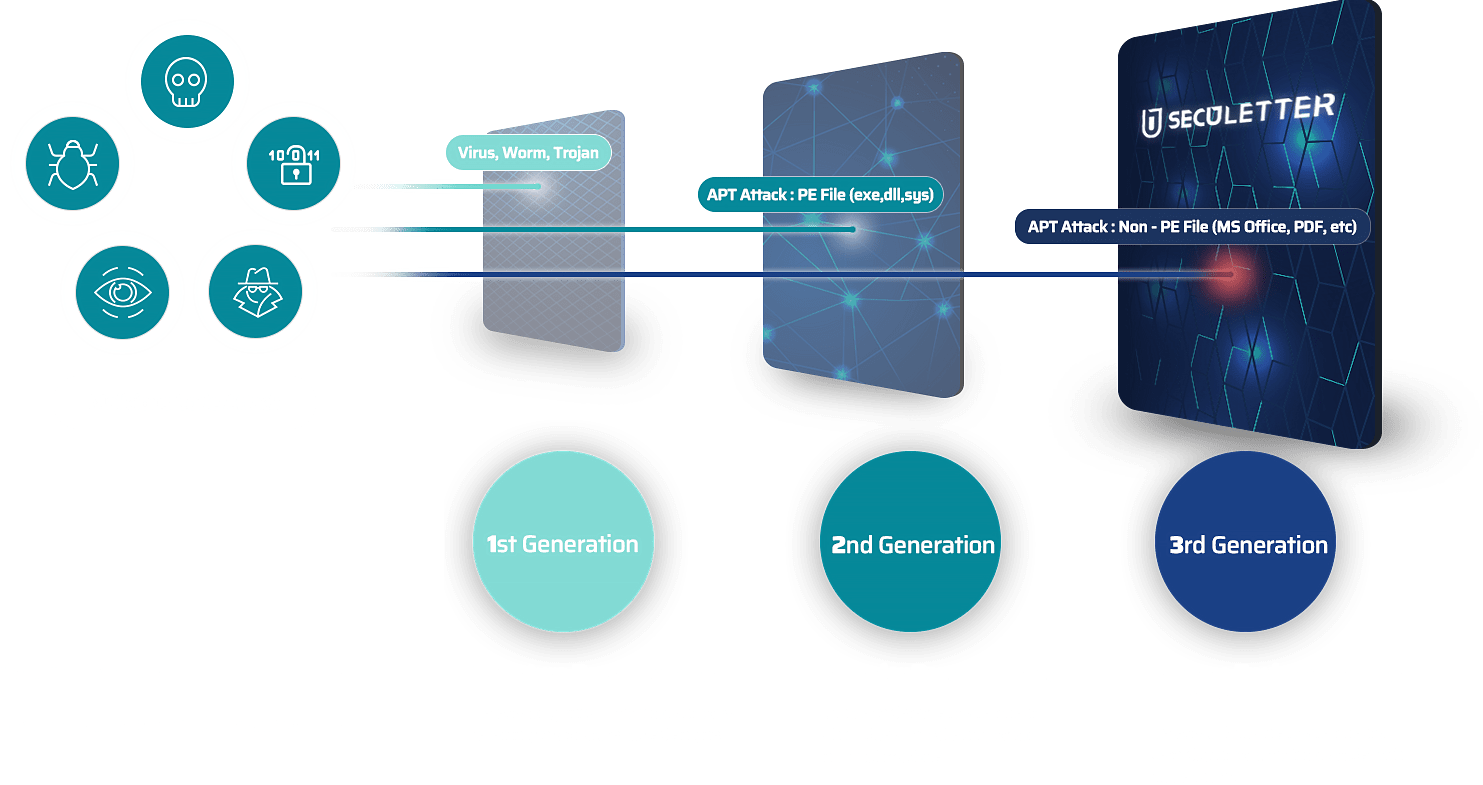
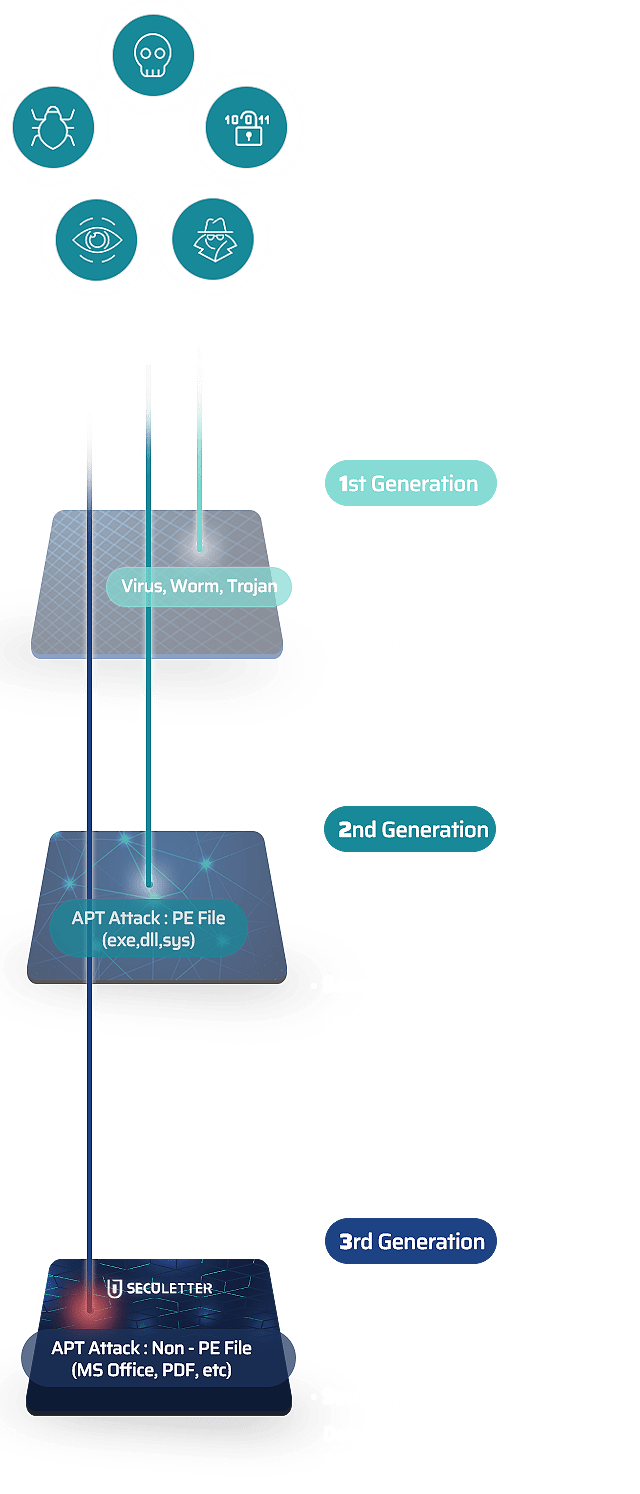
Malicious cyber attacks are evolving. Threat techniques which can evade existing security systems are increasing day by day.
Detecting and blocking the new and unknown pattern requires new cutting-edge technology.