DISARM
Content Security for EmailBlocks new or variant malicious code, ransomware and other unknown persistent threats entering to Microsoft 365
in real time.
Have a question or need our help? Ask us anytime. We will get back to you as soon as possible!
Try and see how many malicious codes your business is exposed to everyday.

Blocks new or variant malicious code, ransomware and other unknown persistent threats entering to Microsoft 365
in real time.
Of all cyberattacks, 75% of advanced security threats are delivered via email, and
72% of these attacks use non-executable files(documents).
DISARM quickly and accurately diagnoses malicious files attached to email, and
proactively removes potential threats from documents and delivers them in safe files.
Removes active content in attachments, such as malicious URL, JavaScript, Shellcode, to response to potential threats with zero trust security-based content disarming (CDR) technology.
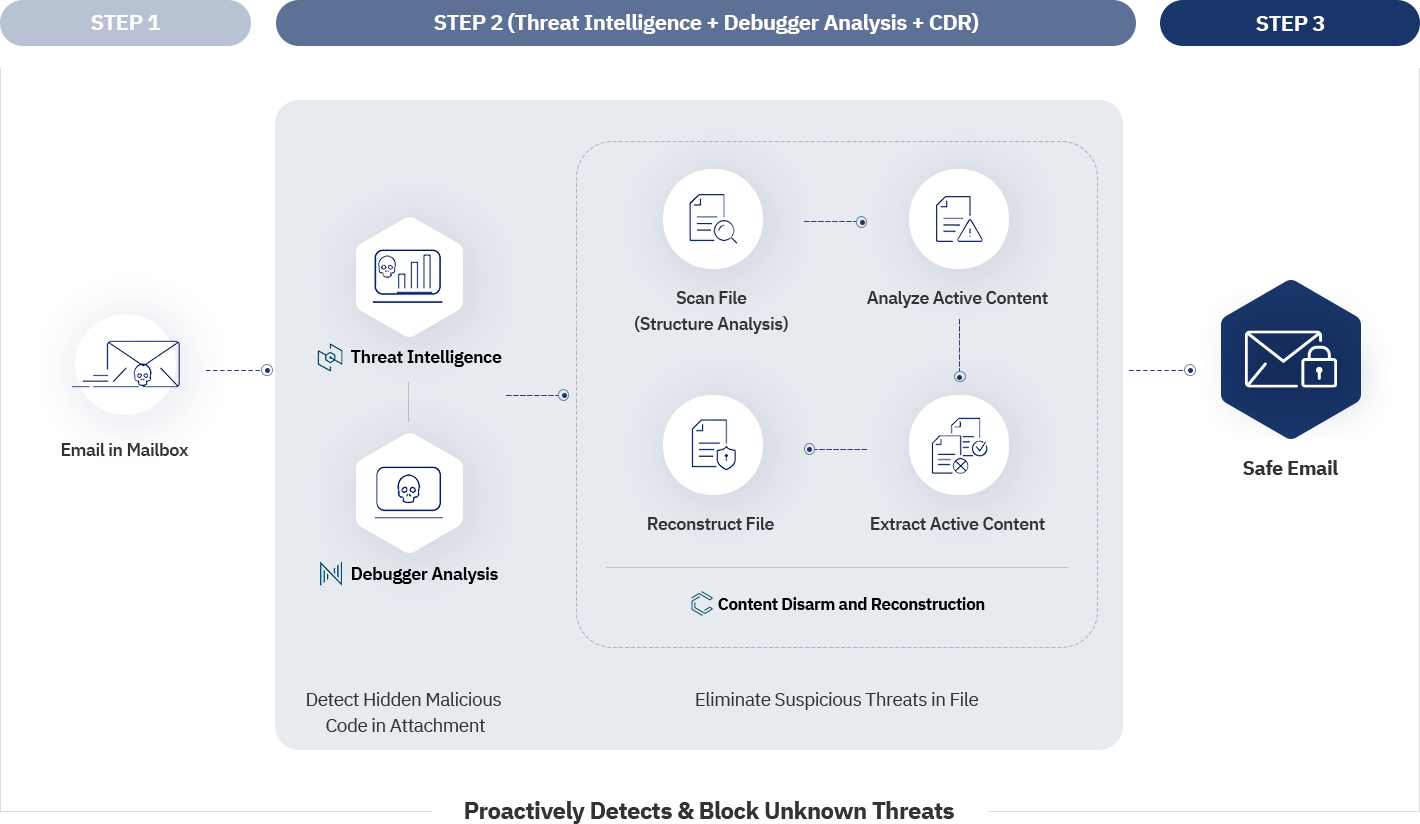
DISARM Content Security (Threat Intelligence + Debugger Analysis + CDR) accurately and quickly detects and proactively blocks not only known security threats, but also unknown security threats that bypass standard Microsoft 365 security features.
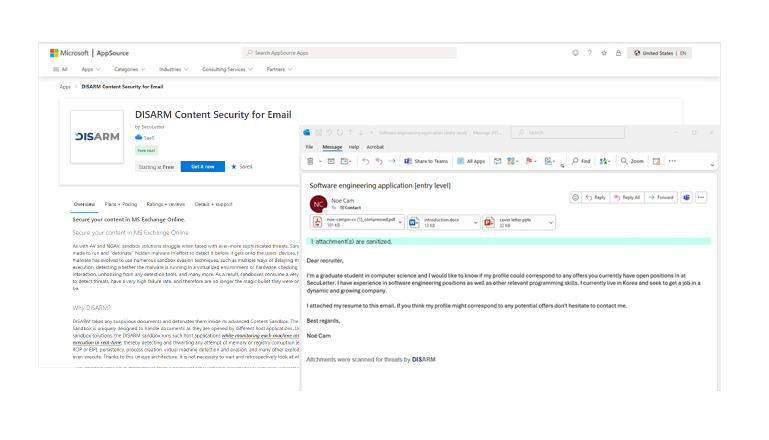
Efficiently manage the service by integrating with your Microsoft 365 account in minutes.

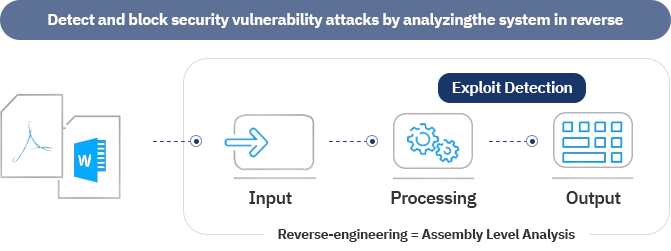
Detect and diagnose malicious code and ransomware in various files, including executable and non-executable files.
Detect and block email phishing attacks by identifying attached malicious files.
Provide detailed analysis information of non-executable files to malware analysis experts.
Discover C&C servers, malicious code repositories, and hacking routes.
Scan entire compressed files for malicious code. (Support ZIP, 7Z, ARJ, RAR, TGA,etc.)
Proactively removes malicious active content from documents and reconstructs them as close to the original as possible. (Support for doc/docx/docm/rtf, xls/xlsx, ppt/pptx/pptm, pdf, image files)
Diagnose spam and phishing email using artificial intelligence and machine learning-based technology.
Extract malicious URL from attachments and email body to diagnose and block security threats.
Prevent threats via debugger engine when files are transferred or shared.
Analyze sender relationships to identify safe senders.
Provides threat intelligence to quickly respond to security threats by managing various content-based information.
Detect and block known and unknown security threats via reverse engineering-based debugger analysis.
How does installing the DISARM Content Security service apply Zero Trust CDR to Microsoft 365?
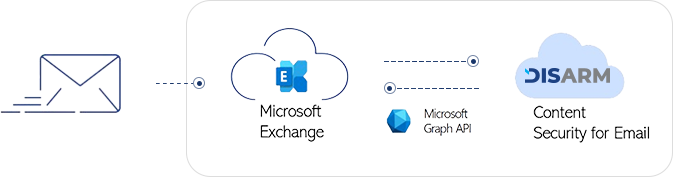
DISARM Content Security service scans emails received by subscribers for the presence of malware and sanitizes attachments before delivering them to the inbox in Microsoft 365. Subscribers are informed that the content has been sanitized via a notification bar at the top of the email body. In the event that a subscriber receives a malicious email, they are notified of the detection results that DISARM Content Security quarantined.
What if my organization already has Microsoft security in place?
Microsoft 365's security features provide signature-based security (e.g., anti-virus, spam, etc.), which makes it challenging to detect and block "Unknown and new variants of malware or ransomware" (Unknown Threat) that bypass traditional security systems. In contrast, DISARM Content Security proactively detects and blocks both known and unknown security threats through proprietary ‘Assembly Instruction Analysis’ technology. Furthermore, DISARM Content Security's CDR technology renders all business content (MS Office, HWP, PDF, JPG, PNG, etc.) harmless to cyberattacks, enabling subscribers to use a more secure Microsoft 365.
How do I install the DISARM Content Security service?
Simply select the subscription plan of your choice on the Microsoft AppSource "DISARM Content Security for Email" page and you're ready to go. For more information, visit the Microsoft AppSource "DISARM Content Security for Email" page.